By Jeremy Onyan, Director, TIme Sensitive Networks, Orolia
Cybersecurity is critical to all facets of the internet. Companies spend millions on cybersecurity every year. Still, often-overlooked areas degrade security. A key example of this is time.
Time plays an essential role in synchronizing core business and network systems. It supports authentication protocols as well as accurate log files critical for an audit trail — necessary for any cyber forensics program. As such, synchronization is often a requirement for network security standards.
A deployment of network time protocol (NTP) synchronizes a local system to a time server. The time source can come from within the network or outside of it.
NTP over the internet. NTP time servers are widely available on the internet. National authorities operate internet time servers based on extremely accurate atomic clocks, such as the National Institute of Standards and Technology (NIST) or the U.S. Naval Observatory.
But even with these sources, many factors impact traceability. According to ntp.org, “If business, organization or human life depends on having correct time or can be harmed by it being wrong, you shouldn’t ‘just get it off the internet’.”
One problem with time synchronization is the variability of network conditions. Network load, variable path delays and firewall settings can impact time quality on the local system. To illustrate this effect, we can use the time-quality monitoring feature of a time server with a built-in GPS receiver as its reference that is accurate to tens of nanoseconds. NTP can be used to compare it to another GPS time server on a local area network. The offset is around 15-20 microseconds (Figure 1).
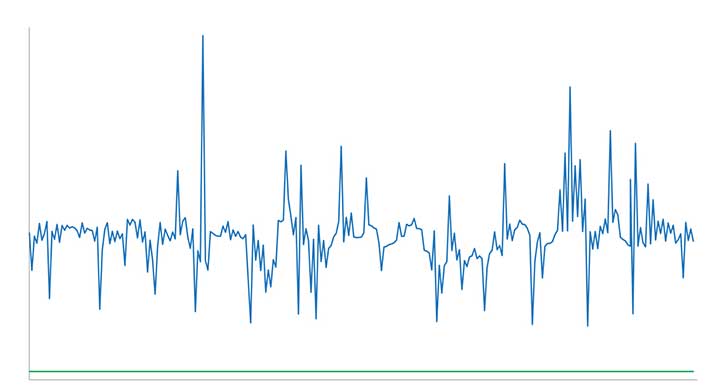
Figure 1. The comparison between two GPS time servers on the same LAN using NTP results in 15–20 microseconds offset. (Chart: Orolia)
We connected the SecureSync time server to some of the most popular internet time servers. The variation result, shown in Figure 2, is as high as tens of milliseconds — 1,000 times worse than NTP across a local area network. If we assume all the time servers are accurate, then the difference is solely due to greater path delay and other dynamic conditions. This variation is enough to question the traceability of time from the internet.
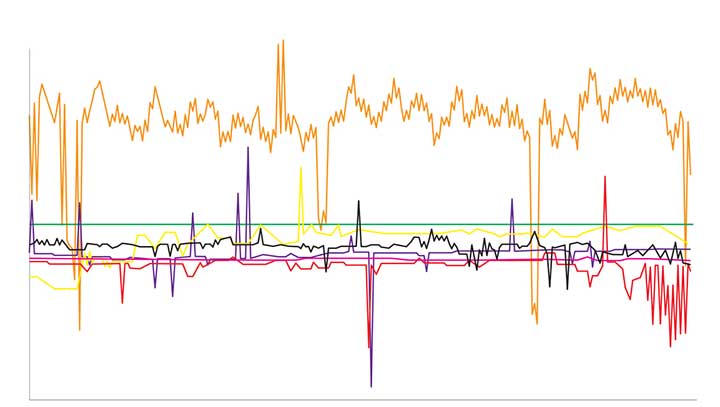
Figure 2. The comparison of internet time servers as measured by NTP on a local GPS time server. The scale is 1,000 times greater than in Figure 1. (Chart: Orolia)
The internet obscures time traceability. Perhaps more important for a security-critical network is the validity of the source used by the time server that distributes time to your network. Time from GPS/GNSS signals is recognized as the most accurate, available and traceable time source.
GPS/GNSS-based time servers are easy and simple appliances to add to the local network. Even when different GPS/GNSS time servers are deployed in different locations, they will provide the same time regardless of geography. What’s more, GPS/GNSS as a local time source can be monitored, so its logs can become part of the audit trail.
Of the seven internet time servers monitored over a 24-hour period, 20 different time sources were identified. Less than half of the sources could be identified as coming directly from GPS/GNSS. In one case, GPS/GNSS time was distributed through three different time servers.
The best practice of using NTP server pools is one reason why there are more sources than time servers. Server pools rotate among various internet time servers, each with their own source of time, to reduce the chance of one bad or unavailable time server catastrophically affecting the synchronization. But this is a problem for traceability. The source of time is not known, nor can it even be determined.
Indeterminate source identification, indeterminate accuracy variation and the inability to log the resulting time synchronization calls into question the efficacy of getting time from the internet. Internet time servers are also subject to being spoofed (bad NTP data sent from a faked IP address) and to direct attacks, including NTP poisoning, replay and denial of service.
When there is a business-critical need to trace time to an accurate source, a GPS/GNSS-based time server should be deployed on the local network.